How WannaCry compromised IT security worldwide
Basic information about WannaCry
It is a virus that spread to at least 74 countries four most affected ones were Russia, Ukraine, India, and Taiwan as of Friday, 12 May 2017, targeting Russia initially and spreading to various industries including telecommunications, shipping, car manufacturers, universities, and health care industries. The malware encrypts user files, demanding a fee of either $300 or $600 worth of bitcoins to an address specified in the instructions displayed after infection. Figure 1 shows the message that infected systems saw when WannaCry compromised devices. This screenshot is from the LogRhythm Labs report. The virus spread was highly effective as it targeted several important and high-profile entities, including several entities in the UK, including the National Health Service (NHS).
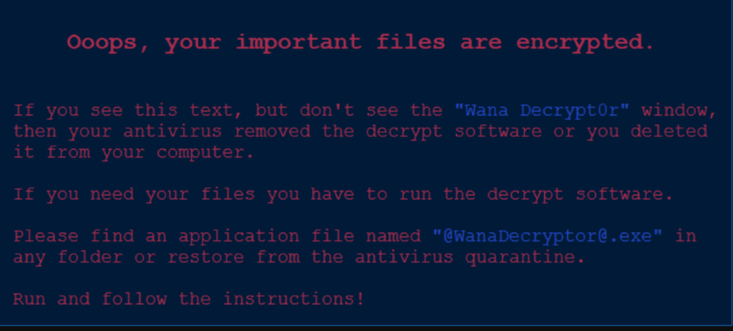
Figure 1
WannaCry components and source
The WannaCry ransomware is composed of an initial dropper containing the encrypter as an embedded resource. The encrypter components are:
- a decryption application (“Wana Decrypt0r 2.0”)
- a password-protected zip containing a copy of Tor
- several individual files with configuration information and encryption keys.
There was speculation that an infected PDF file was the source of the attack, which was used later in a phishing campaign. However, analysts have not confirmed this theory, and until now, we are not 100% sure about the initial source of the attack.
How did WannaCry infect systems?
The source code of WannaCry has not been found till this moment, and it is not available to researchers. Researchers used behavioral patterns of the virus to assess its interaction with systems. They speculate that:
- The virus tries to access a hard-coded URL which is a kill switch.
- If WannaCry could connect to the URL, it shuts down, while if it can’t, it continues searching and encrypting files within the system that has a particular extension, like Microsoft Office files to MP3s and MKVs.
- After encryption, files become inaccessible to the user of the device. Then the screen shows a window demanding the user to pay an amount of either 300$ or 600$ in Bitcoin to decrypt the files and make them accessible again (please see Figure 2).
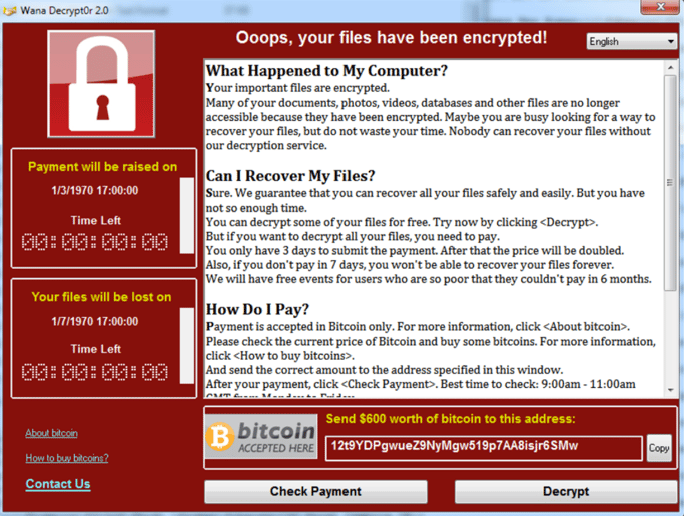
Figure 2
NHS – A prominent high-profile victim of WannaCry
As already stated, many institutions were affected by this virus. A prominent stand as one of the WannaCry victims was the NHS in the UK. On the 12th of May, NHS initially identified 45 NHS organizations, including 37 trusts infected by the WannaCry ransomware. Over the following days, more organizations of the NHS reported that they had been affected as well. In total, 80 out of 236 trusts across the UK were involved.
As a result, the NHS reported the following numbers:
- 34 infected and locked out devices and
- Forty-six disrupted systems that were later proved to be uninfected. Systems were disrupted because they were shut down as a precaution causing email and other services to stop working. As a result of this measure, employees had to use pen and paper for activities usually performed electronically.
The cyber-attack could have caused more disruption if it had not been stopped by a cyber researcher activating a ‘kill-switch.’ On the evening of the 12th of May, a cyber-security researcher activated a ‘kill-switch’ so that WannaCry stopped locking devices. This meant that the WannaCry ransomware had infected some NHS organizations, but because of the researcher’s actions, they were not locked out of their devices and systems. Between the 15th of May and mid-September, NHS Digital and NHS England identified additional 92 organizations, including 21 trusts, as contacting the WannaCry domain. NHS England believes more organizations were infected in these regions because they were hit on 12 May before the WannaCry ‘kill-switch’ was activated.
WannaCry Mitigation and Prevention
Suppose a system becomes infected with the WannaCry ransomware. In that case, it is best to try to restore files from backup rather than paying the ransom, as there is no guarantee that payment will lead to successful decryption.
To prevent infection and the spread of this malware across the network, all Windows systems should be updated on current patches and antivirus signatures. Additionally, blocking inbound connections to Server Message Block (SMB) ports (139 and 445) will prevent the spread of the malware to systems still vulnerable to the patched exploit.
For further guidance, refer to the following Microsoft blog article, which references an emergency patch issued for customers running unsupported operating systems.
Ransomware in Germany
Ransomware attacks struck Germany as well. One example is the University Hospital Düsseldorf. In 2020, IT systems were encrypted by a ransomware attacker known as DoppelPaymer, forcing the hospital to reject emergency patients and making this attack possibly the first instance of death by ransomware after a patient died while critical hospital systems were offline due to the ransomware attack.
Please check this report for further information regarding the history and the trend of Ransomware attacks in 2021 and 2022.
WannaCry in Germany
WannaCry didn’t spare Germany. It infected Deutsche Bahn computers. Train passengers could see it on the screens and the display boards of various train stations. Figure 3 shows the infection message displayed on the screens in the train stations according to heise.de. The cameras at the train stations were also affected.
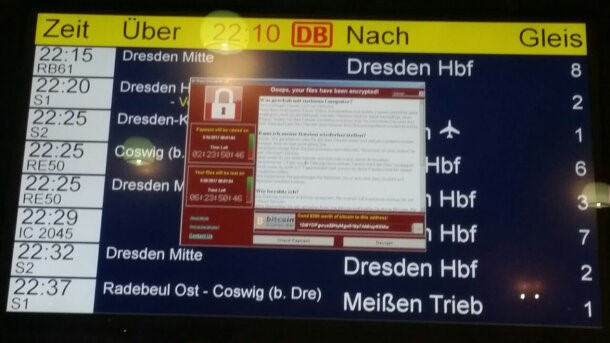
Figure 3
According to the Federal Ministry of the Interior, video surveillance at train stations was also affected, while the computers of the federal police themselves were not.
WannaCry appeared on the display boards of several DB stations, including Frankfurt Central Station. Though DB planned trips and trains schedule went normal, ticket machines stopped working due to the infection of the computers they run.




