Information security and IT protection goals "availability, integrity and confidentiality" are not solely relevant for security experts, but are increasingly important for management due to the holistic significance of information security for companies of any size. This is related to the strong networking in companies and organizations and the increasing threat of attacks or other foreign interference of various kinds. Today, information security is at a higher risk. Nevertheless, information has high value and therefore needs to be protected. In this article, we will explain to you all the essentials about the topic of information security protection goals.
Threats to Information Security
Before we look in detail at the protection goals of information security, let's address the question of what threats exist to information in companies and their systems. From an ISACA study, the top 10 technology risks were evaluated by experts from large companies. These are shown in the figure below.
TOP 10 TECHNOLOGY RISKS ACCORDING TO ISACA
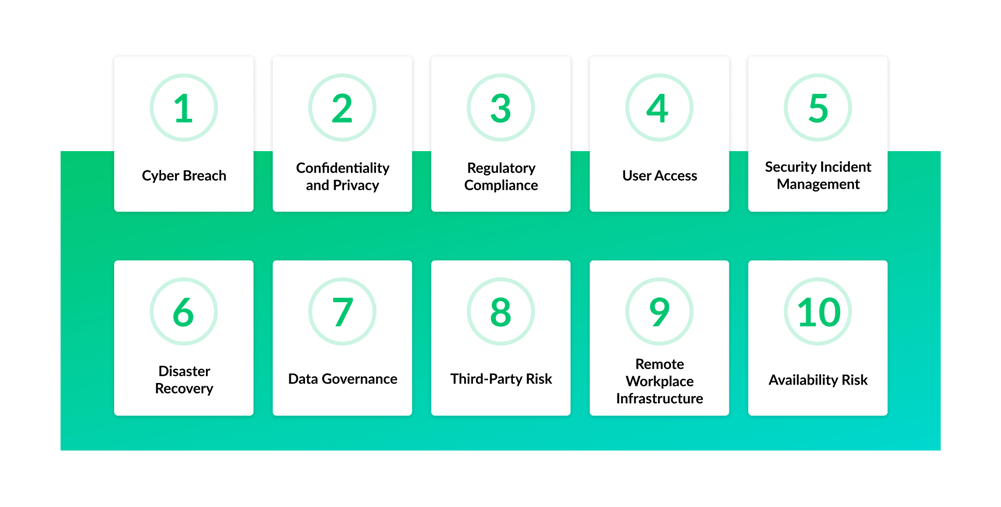 These include, for example, in 1st place cyber-attacks, which are appearing more and more frequently but may go unnoticed for a long time. A characteristic example in this context is the critical vulnerability in log4j recently rated by the BSI as IT threat level 4 / red. Cyber attacks represent targeted attacks on a company's corporate network. These take place, for example, through malicious codes, malware, hacking attacks, or spam.
These include, for example, in 1st place cyber-attacks, which are appearing more and more frequently but may go unnoticed for a long time. A characteristic example in this context is the critical vulnerability in log4j recently rated by the BSI as IT threat level 4 / red. Cyber attacks represent targeted attacks on a company's corporate network. These take place, for example, through malicious codes, malware, hacking attacks, or spam.
A number of cases that have come to light in the media have made it clear that the involvement or cooperation of employees can also jeopardize information security. This can be countered by numerous countermeasures, such as training/education on information security, the design of IT and compliance guidelines, and also by measures to promote employee loyalty.
Another form of threat to information security, often disastrous in its impact, is an "act of god." It usually includes environmental and weather disasters (water, fire, storm) outside of human control, i.e., evens for which no person can be held responsible. This type of threat can lead to a partial or complete interruption of business operations because data centers that process important information may be affected by the disaster. In this context, the term business continuity management (BCM) often comes up. Within the framework of BCM, plans are defined as to how regular operations can be resumed in the shortest possible time after an interruption caused by disruption.
Laws, standards and regulations in this context aim to develop a (legal) framework for the adequate protection of critical data and information. Examples are e.g. GDPR or the IT Security Act. Data does not have to be solely electronic in nature but can include any written and printed information that is transmitted by non-electronic means (e.g., postal mail) or archived. Information security is therefore dedicated to protecting all data, whether in digital or non-digital form.
Protection Goals according to ISO/IEC 27001
The concept of information security is the subject of the ISO/IEC 27000 series. In the main document of ISO/IEC 27001, information security is defined by the IT protection goals of confidentiality, integrity and availability. Other factors that can also be part of information security according to ISO/IEC 27000 are authenticity, accountability, non-repudiation and reliability.
Core Protection Goals of Information Security
i. CONFIDENTIALITY
The protection goal of confidentiality refers to the protection against the leakage of information or confidential data. This includes, for example, turnover or sales figures, key marketing figures, research and development results, etc., which could be of interest to competitors. According to the BSI, confidentiality is breached when confidential information is accessed or disclosed without authorization. Confidentiality is therefore intertwined with the concept of authenticity. The interlocking of confidentiality and authenticity is expressed by the fact that it must be ensured by defining authorizations and controls that unauthorized users are not allowed to obtain knowledge of confidential information.
ii. INTEGRITY
The German Federal Office for Information Security defines the protection goal of integrity in basic IT protection as the functioning of IT systems without exception and the completeness and correctness of data and information. If we relate the protection goal to information security, integrity means preventing unauthorized changes to important information. Manipulative changes, such as inserting or deleting characters, changing an arrangement of data or files, or duplicating information, lead to the violation of this protection goal. Through (additional) attributes, such as author, date of setting, date of the change, etc., changes to the information can be traced. Falsified data leads to errors in the company, which can quickly cause major damage (financial and/or reputational). These manifest themselves, for example, through incorrect bookings, incorrect deliveries, or faulty products.
iii. AVAILABILITY
The protection goal of availability is met when IT systems, IT applications, IT networks or electronic information are available to a user (e.g., employees or customers). Availability is used as a measure to describe the performance that an IT system must deliver at a given time. A breach of availability becomes noticeable when, for example, data or information (e.g. invoices, customer data, marketing data, etc.) is not retrieved from the computer (PC, laptop, smartphone, etc.) or financial transactions are not carried out. A variety of other impact scenarios are conceivable depending on the business process: Online purchases can no longer be processed, machinery or entire production facilities fail. These examples show that a breach of availability can lead to high financial damage for a company as well as damage to its reputation.
CIA Triad
Combining the protection goals of confidentiality, integrity and availability forms the InfoSec CIA triad.
Beyond InfoSec CIA Triad
Beyond the InfoSec CIA triad, people have been extending the basic principles with additional security concepts like: non-repudiation, awareness, privacy, risk, traceability, etc. These concepts are sometimes added as additional attributes. Next, we discuss some of these attributes.
- Authenticity: It refers to the assurance of the authenticity and credibility of an object, which can be verified on the basis of a unique identity and characteristic properties. Only with a functional authentication can data be assigned to its origin and a role assignment of authorization be possible.
- Liability/Non-Repudiation: This goal involves ensuring that a message sent must be verifiable and provable. More precisely, this means that communication cannot be subsequently denied to third parties by one of the subjects involved. This goal is particularly important for service providers.
- Accountability: This refers to protection against intentional or unintentional disruptions, for example, due to attacks or even force majeure. It is associated with control activities securing the architecture, its processes and reducing overall complexity. Regular controls ensure that all security measures (both technical and operational) are working as intended to protect the system and the information processed within it.
Protection Requirement Categories for Classification of Security Requirements
The need for the protection of an asset with regard to a protection goal is based on the extent of the damage in the event of a breach. The extent of the damage cannot be determined exactly in advance. As an alternative, it is often recommended to define protection requirement categories, which allow for the classification of the impact of damage in the event of a breach of the respective protection goal. The German Cyber Security Authority for instances names the following three protection requirement categories:
- normal: The damage effects are limited and manageable.
- high: The damage effects can be considerable.
- very high: The damage effects can reach an existentially threatening, catastrophic extent.
The damage that can result from a violation of the protection goals can relate to various damage scenarios:
- violations of laws, regulations, or contracts,
- impairment of the right to informational self-determination,
- impairment of personal integrity,
- impairments of the performance of tasks,
- negative internal or external impact, or financial impact.
Related Article Announcement: White Paper Information Security: A Holistic Approach