Cloud computing audit guidelines of Cloud Security Alliance
As the popularity of cloud computing has increased over the last decade, so has the maturity of standards used to govern these resources. It is thus of vital interest to define cloud computing and the peculiarities of a cloud computing audit with the focus on state-of-the-art auditing guidelines of the cloud security alliance (CSA).
What is Cloud Computing?
A solid definition of cloud computing is provided by the National Institute of Standard and Technology (NIST). The definition is as follows:
“Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.”
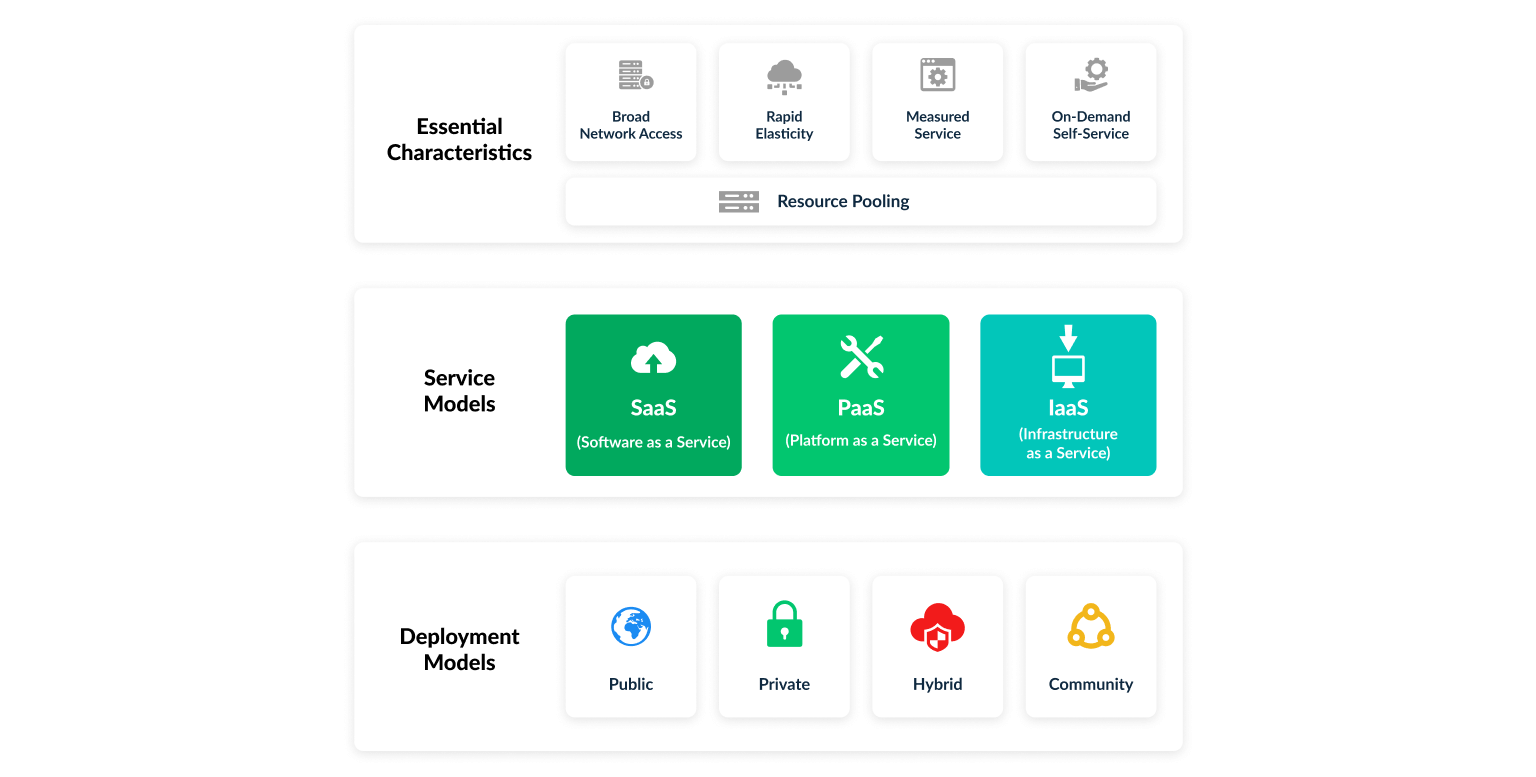
To put in more layman's terms: Cloud computing refers to the use of IT resources via the Internet. Data is not stored locally on a user's own PC but instead located at any other place, which is often illustrated with a data cloud. This has given rise to the term "cloud computing". In the aforementioned document, NIST authors discuss five essential characteristics, three service models and four deployment models that apply to the cloud model. The following illustration summarizes this aspect in greater detail.
A sometimes confusing aspect is the distinction between the three service models - SaaS, PaaS and IaaS - of cloud computing. In the case of "Infrastructure-as-a-Service" (IaaS), users can access individual virtual resources, such as storage, servers, network components, directly via the Internet. "Software-as-a-Service" (SaaS) allows users to use software applications over the Internet without installing them on their PC. "Platform-as-a-Service" (PaaS) is particularly interesting for developers who want to jointly develop and offer programs over the Internet.
Why the interest in Cloud Computing?
For companies, this approach offers in general flexibility, scalability and mobility. Some of the main advantages for companies are the following:
-
They tie up less capital in hardware and software licenses and still get a highly flexible infrastructure that can be adapted to new requirements at any time.
-
They transfer the installation and maintenance of their IT systems to specialists and can concentrate on their core business.
-
The same data can be accessed from different locations and by different people. Employees can therefore also process company data on the move using mobile devices such as smartphones and tablets.
Basic rules of Cloud Computing
In the context of cloud computing, specifically for the more risk-involved deployment models, data should always be transferred via an encrypted connection. Of highest priority are particularly sensitive information for which special measures have to be taken. This is where the choice of the cloud provider does matter. Only specialized cloud providers adapted to the requirements of the type of data or the industry in question should be used.
In addition, the basic rules for secure IT use apply. This means, among other things, that passwords must be secure and should be changed regularly. Attention must also be paid to good data backup. Reputable cloud computing providers usually back up the data several times. A regular local backup offers additional protection. Such backup ensures access to data in cases when the Internet connection is interrupted.
What is Cloud Compliance?
Cloud compliance refers to meeting the requirements or criteria needed to be in accordance with a certain type of certification or framework. There are a variety of different types of compliance that may be required by industry, request for proposal, client, etc. The type of cloud security and compliance requirements will help determine the cloud compliance that is right for an organization.
SOC 2, for instance, as an examination of control procedures in service-providing IT organizations does not have any specific requirements on cloud compliance. However, it requires the implementation of logical access security software, infrastructure and architecture over information assets to protect them from security threats. Controls are enabled as a means to provide evidence of (cloud) compliance and proper implementation standards, e.g. control access to sensitive information, data encryption and regular patching. Compliance programs such as FedRAMP, Cloud Security Alliance (CSA), HITRUST, ISO 27017, and PCI focus on standardizing frameworks for security assessment, authorization, and continuous monitoring of cloud products and services.
Auditing in Cloud Computing
During the planning and execution stages of a cloud security and compliance audit, it is vital to develop a thorough understanding of all relevant audit objectives. Ideally, companies should align their business objectives with the objectives of the audit. ISACA as an independent organization works in the development, adoption, and use of globally accepted, industry-leading knowledge and practices for information systems. An excellent list of objectives for cloud computing is ISACA’s IT Control Objectives for Cloud Computing: Controls and Assurance in the Cloud.
CSA Cloud Controls Matrix (CSA CCM)
The cloud security alliance (CSA) is the world’s leading organization in defining best practices to help establish a secure cloud computing environment. Since 2010, the CSA has released multiple versions of a Cloud Controls Matrix (CCM) for public use. The latest version (v4.0) was released in July 2021 with SRCs managing directors Jan Jacobsen and Bilal Khattak being the lead authors.
The CSA CCM is a cybersecurity control framework for cloud computing aligned to the CSA best practices - the de-facto standard for cloud security and privacy. The accompanying questionnaire, CAIQ v4, provides a set of yes/no questions based on the security controls in the CCM. The CCM and CAIQ can be downloaded through the following useful link. CSA’s cloud control matrix allows service organizations to identify the controls they should have in place in order to prepare for various engagements.
CSA CCM Domains
In chapter 2 of CSA CCM v4.0 the auditing guidelines of 17 domains are described which altogether form CSA’s current cloud controls matrix. Note that each domain contains a set of controls. As part of each control, the control title, its ID, the control specification and the control-specific auditing guidelines are provided. The 17 domains CSA states are given in the following table:
|
CCM Domain |
# of controls |
|---|---|
|
Audit & Assurance (A&A) |
6 |
|
Application & Interface Security (AIS) |
7 |
|
Business Continuity Management & Operational Resilience (BCR) |
11 |
|
Change Control & Configuration Management |
9 |
|
Cryptography, Encryption & Key Management |
21 |
|
Datacenter Security (DCS) |
15 |
|
Data Security & Privacy Lifecycle Management (DSP) |
19 |
|
Governance, Risk Management and Compliance (GRC) |
8 |
|
Human Resources (HRS) |
13 |
|
Identity & Access Management (IAM) |
16 |
|
Interoperability & Portability (IPY) |
4 |
|
Infrastructure & Virtualization Security (IVS) |
9 |
|
Logging and Monitoring (LOG) |
13 |
|
Security Incident Management, E-Discovery, & Cloud Forensics (SEF) |
8 |
|
Supply Chain Management, Transparency, and Accountability (STA) |
14 |
|
Threat & Vulnerability Management (TVM) |
10 |
|
Universal Endpoint Management (UEM) |
14 |
Cloud Security Alliance Guide
The Cloud Security Alliance Guide v4.0 is a document that can be downloaded from the Cloud Security Alliance website through the link here. Briefly speaking, the guide provides additional educational information to organizations on how they can safely adopt cloud services, as well as identify and address the underlying risks.
Summary
This article tried to give a short, but still comprehensive overview of cloud computing and underlying aspects with respect to auditing and compliance. In addition to that, the CSA CCM v4.0 was introduced. The CSA CCM v4.0 is the most recent cloud security matrix (CCM) developed by the cloud security alliance (CSA) - the world’s leading organization in formulating best practices on secure cloud computing - to help organizations evaluate their cloud security posture and implement best practices.
If you have any additional questions regarding the many services we offer at SRC Consulting, including but not limited to network security, information security audit and cloud security, please do not hesitate to contact us.