All you need to know about ISO 27001
The rapid digital transformation emerged the need to consider safe cyber systems that respond to the needed technical developments while preserving the security of the information system of institutes/companies.
The International Organization for Standardization (ISO) together with International Electrotechnical Commission (IEC) formed the Joint technical committee (JTC) which produced later the international standard of the Security Management System called ISO/IEC 27001.
The ISMS is a system that preserves the confidentiality, integrity, and availability of a system that forms the CIA triad. Recall that the CIA triad is described in one of our previous blog articles. ISMS provides an overall security management system to ensure that institutes are protected up to specific standards.
ISO 27001 is one of the most prominent standards due to its international recognition and because it involves auditing and certifications, while other standards like the Cyber Security Framework (CSF) published by the National Institute of Standards and Technology (NIST) are voluntary ones.
ISO 27001 deals mainly with risk management. It provides a general guide to implementing a strong ISMS for companies keen to operate in a secure environment. It concentrates on the risk assessment, treatment, and verification processes.
Though ISO/IEC 27001 certification in many cases is not a must, it is highly recommended that any business would adapt to its standards. ISO/IEC 27001 focuses on people, processes, and technologies formulating holistic guidelines that any industry can abide by combat the security gaps that could compromise its cyber system.
BS 7799-3 is a standard published by the British Standards Institution (BSI) and aims to provide a guideline for implementing ISO/IEC 27001. Below figure shows the implementation model in reference to BS 7799-3 standard:
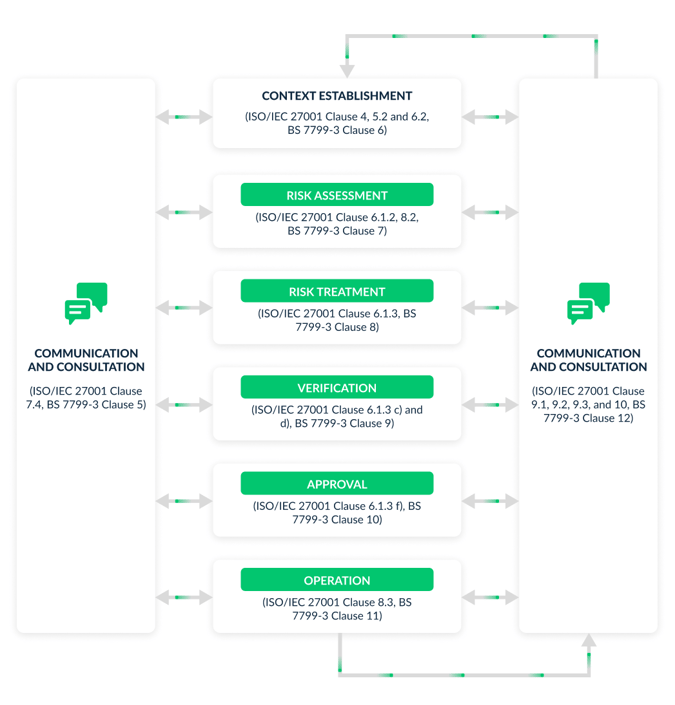
Figure 1
Figure 1 specifies the implementation steps of ISO 27001 in particular the 6.1, 7.4, 8.2, 8.3, and 9 clauses. For the interested reader, we recommend reading BSI guidance documents for further details about the implementation of each clause. Also, check our recent SRC blogs as we are planning to elaborate on each clause in greater detail in the future.
In reference to ISO/IEC 27001, risk assessment is a mean/practice aimed to identify, assess, and prioritize the potential risks in the risk space. Instead of tackling all risks in the risk space, proper risk assessment makes the efforts concise toward specific risks that are relevant to the industry context. For example, a DoS attack is less likely to be considered if a company/business doesn’t carry a political agenda or is not a part of a conflicting context.
For further information, please revisit our catalog of reference measures blog.
Risk assessment involves measuring all the identified risks on the scale of impact/frequency to give priority to those who score high/ very high.
After assessing company-specific risks, ISO/IEC 27001 guides making a treatment plan that responds to the identified and prioritized risks. Having said that, ISO/IEC 27001 suggests the most feasible treatment within its (Annex A) which contains the necessary controls linked to the identified risks.
Later stages elaborate on the verification process of discussing and comparing the chosen controls with those that exist in (Annex A). If approved/verified, then they can be put in place for operation as shown in Figure 1.
The general benefits of ISO/IEC 27001 certification:
- Constant secure system: ISO/IEC 27001 builds on a continuous process that iterates through assessment, planning, implementation, and evaluation in a repetitive manner. Such a process ensures that the system is equipped with the latest risk management exercises.
- Risks reduction: ISO/IEC 27001 expects the occurrence of the risks and handles them accordingly. With a good risk assessment/treatment plan, companies can make sure that no surprising risk with a catastrophic impact can emerge.
- Good preparation: incident handling process becomes easier and in control when the potential risks are identified and expected. This will assure a fast recovery and business continuation.
- Integration: The system is more prepared to adapt to new controls by building up on the current information security blocks. In this case, scalability and optimization are in hand.
- Certification brings trust: Handling customers' data securely with a proper system in place brings the trust of the customers and 3rd parties.
Figure 2 shows the 14 domains of ISO 27001:
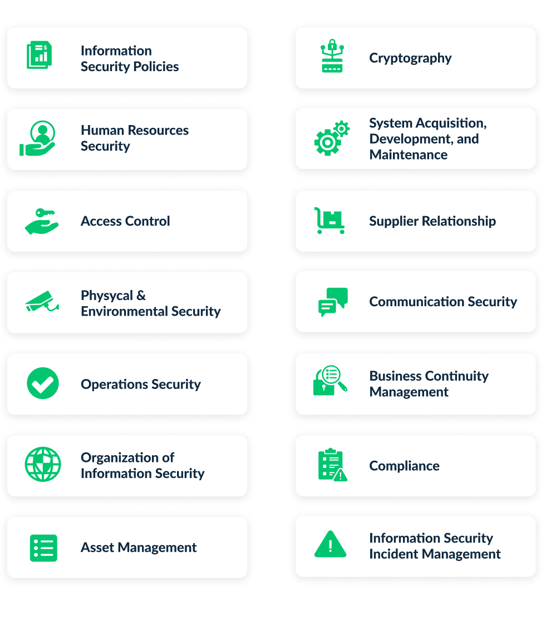
Figure 2
SRC offers comprehensive compliance consulting to the ISO/IEC 27001 which is increasingly becoming of vital interest for businesses in different fields. Implemented by its experts, SRC starts by helping apply a full risk assessment exercise to select and prioritize risks qualified for treatment.
Also, SRC suggests the most relevant and up-to-date controls for the risks identified by following the latest technologies and practices. SRC compares the suggested controls with the applied ones and provides the best practice regarding the assessed risks and expected expenditures. For instance, SRC will suggest only the relevant controls that achieve the best value without engaging companies in expensive controls with a limited protection impact.
By providing an extensive report, SRC experts make sure that ISO/IEC 27001 standard is fully applied and in accordance with international level of applicability and usability.